
- Cryptography Tutorial
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Symmetric Algorithms
- Data Encryption Standard
- Triple DES
- Advanced Encryption Standard
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Cryptography Useful Resources
- Cryptography - Quick Guide
- Cryptography - Discussion
Cryptography - Cipher Block Chaining (CBC) Mode
It is a A block cipher that encrypts a series of bits as a whole or as a block and applies a ciphertext or encrypted key to the full block of cryptography is known as a cipher block chaining (CBC) mode. Initialization vectors (IVs) of particular characters in length are used in cipher block chaining. One of its main features is that it makes use of chaining, a working technique that makes a ciphertext block's decryption dependent on every block that came before it. Therefore, the cryptography of the block that comes right before the ciphertext has all of the validity of all blocks that came before it.
A single-bit cryptography error in one block of ciphertext affects all subsequent block decryptions. The ciphertext blocks' order can be changed, which corrupts the decryption process. In cipher block chaining, each plaintext block is essentially encrypted using cryptography after being XORed (see XOR) with the block of ciphertext that comes right before it.
Only when the same plaintext or original text block is encrypted with the same encryption key and the initialization vector (IV) and the ciphertext block order is left unaltered will the identical ciphertext blocks provide the desired outcome. Because the XORing process masks plaintext patterns, it has an advantage over the Electronic Code Book mode.
When two communications are encrypted using the same encryption key, the initialization vector (IV) should differ. While some applications may find it useful and unique, the initialization vector does not necessarily need to be stored or kept secret.
Since ECB compromises some security or privacy criteria, cipher block chaining, or CBC, is an improved or more sophisticated version of ECB. After XORing with an initial plaintext block of the cryptography, the preceding cipher block in the CBC is sent as input to the subsequent encryption process. To put it simply, an XOR output of the previous cipher block and the current plaintext or original text block is encrypted to create a cipher block.
The process is shown below −
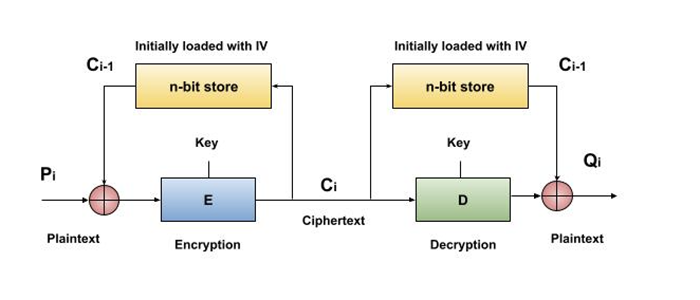
Operation
The above image shows how the CBC mode works. The following are the steps −
The top register should be loaded with the n-bit Initialization Vector (IV).
XOR the data value in the top register with the n-bit plaintext block.
Use key K to encrypt the output of the XOR operation using the underlying block cipher.
Continue the process until all plaintext blocks have been processed by feeding the ciphertext block into the top register.
IV data is XORed with the first decrypted ciphertext block in order to decrypt it. In order to decrypt the next ciphertext block, the previous ciphertext block is added as well into the register that replaces IV.
Analysis of CBC Mode
In CBC mode, the previous ciphertext block and the current plaintext block are combined, and the outcome is then encrypted using the key. Decryption, then, is the opposite procedure, in which the previous ciphertext block is added to the result after the current ciphertext has been decrypted.
The benefit of CBC over ECB is that an identical message can use a different ciphertext when the IV is changed. On the negative side, the chaining effect causes the transmission error to propagate to a few further blocks during decryption.
It is important to note that CBC mode provides the base for a well-known data origin authentication system. Thus, it benefits applications which need both symmetric encryption and data origin authentication.
Bit-Width of CBC Mode
The following table show the bit-width of the interfaces that CBC mode offer −
| plaintext | ciphertext | cipherkey | IV | |
|---|---|---|---|---|
| CBC-DES | 64 | 64 | 64 | 64 |
| CBC-AES128 | 128 | 128 | 128 | 128 |
| CBC-AES192 | 128 | 128 | 192 | 128 |
| CBC-AES256 | 128 | 128 | 128 | 128 |
A common block cipher mode of operation that makes use of the block cipher algorithm is the Cipher Block Chaining (CBC) mode. It has the ability to process both the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES) in this version. The cipherkey length for AES should be 128/192/256 bits, and 64 bits for DES. Another drawback is that, but text in the real world comes in a range of lengths, our working mode only supports units of a fixed size (64 or 128 bits for a single block). Therefore, before encryption or decryption, the final block of text given to this primitive needs to be padded to 128 bits.
Formula for CBC mode
This method can be expressed as follows if it is put it into a formula −
Ci = EK(Bi ⊕ Ci-1)
where Ci-1 is the cipher that corresponds to Bi-1 and EK is the block encryption technique with key K.
Note: It is assuming that C0 is the initialization vector in the formula above.
In the same way, the CBC can be used for decryption by using −
Bi = DK(Ci)⊕(Ci-1)
Where DK stands for the block decryption technique with key K.
For decryption, the same initialization vector (C0) will be used.
Security Challenge
The primary attributes of this scheme are as follows −
One additional particular block will be damaged if even a single bit of the conveyed message gets altered or lost. This harm wouldn't affect other blocks.
In the event that a bit is lost or added to the ciphertext, the bits and block borders will move, producing an incorrect decoding of all ensuing blocks of the cryptography's ciphertext.
The factor has the ability to append blocks to the end of the deciphered message, thereby enhancing it with either the original or plain text.
Advantages
Cipher Block Chaining (CBC) mode has several advantages −
When input data is more than one block in size (usually 128 bits or 16 bytes for AES), CBC operates well. Messages of any length can be encrypted and decrypted by breaking them up into blocks and joining them.
Although CBC itself cannot provide authentication, it can be used in combination with digital signatures or HMAC (Hash-based Message Authentication Code) in order to ensure the integrity and validity of the encrypted data. CBC can offer a complete security solution by combining authentication and encryption.
When it comes to cryptanalysis, CBC is typically safer than ECB (Electronic Codebook) mode. An attacker finds it more difficult to identify patterns in the encrypted data when using CBC, because each block of ciphertext depends on the one before it. Due to this, CBC is more effective for securing private data from attacks or attempts to decipher it.
Disadvantages
The inability of Cipher Block Chaining (CBC) mode for sending out concurrent encryption is one of its drawbacks. Before encryption, each plaintext block in CBC mode is XORed with the previous ciphertext block. This creates a dependency on the previous ciphertext block for the current block's encryption. As each block's encryption depends on the previous block's encryption being finished, the following ones cannot be encrypted concurrently or in parallel. In comparison to modes like Electronic Codebook (ECB) or Counter (CTR) mode, which can carry out concurrent encryption of numerous blocks simultaneously, the sequential nature of encryption in CBC mode can result in slower encryption performance. But because of its security benefits and compatibility for a wide range of encryption scenarios, CBC mode is still widely used despite of this limitation.
To Continue Learning Please Login