
- Cryptography Tutorial
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Cryptography Useful Resources
- Cryptography - Quick Guide
- Cryptography - Discussion
Cryptography - Block Cipher
Block ciphers and stream ciphers are the two categories into which encryption techniques divide according to the way the input is handled. A block cipher creates a ciphertext the same size by operating on fixed-size input blocks made up of b bits. When the input exceeds b bits, it is broken down into smaller blocks. Block ciphers use a variety of operating modes to deal with different use cases.
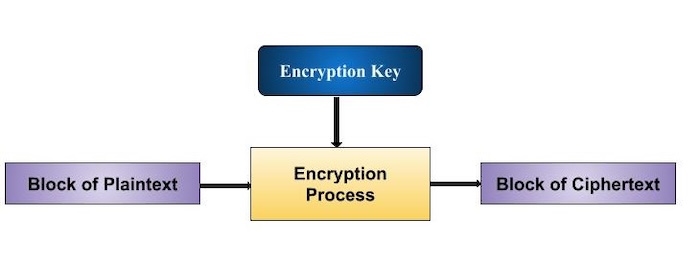
Block Size
While choosing a block size, keep the following factors in mind even if any size block is possible −
Avoid extremely small block sizes − Let's say a block size is m bits. There are then 2m possible combinations of plaintext bits. By creating a dictionary of plaintext/ciphertext pairings sent with that encryption key, the attacker can launch a sort of "dictionary attack" if they find the plain text blocks that match certain previously delivered ciphertext blocks. Because a larger dictionary is required, attacks become more difficult with increasing block sizes.
Avoid using a very big block size − An extremely large block size makes the cipher difficult to use. These plaintexts will need padding before encryption.
Multiples of 8 bits − Since most computer processors handle data in multiples of 8, a multiple of 8 is a preferred block size due to its ease of implementation.
Padding in Block Cipher
Block ciphers operate on fixed-size blocks, such as 64 bits. Most of the time, the length of a plaintext does not multiply by the block size. A 150-bit plaintext, for example, has two blocks of 64 bits each and a third block of 22 bits for balance. To make the final block's length equal to the scheme's block size, additional data must be appended to the last block of bits. In our case, 42 more redundant bits must be added to the remaining 22 bits in order to create a complete block. Padding is the process of adding bits to the final block.
The process is inefficient when there is too much padding. Also, if padding is done regularly with the same bits, it can sometimes leave the system vulnerable.
Modes of Operation
Block cipher modes refer to various techniques for using secret codes for encryption and decryption. Consider a message encrypted into scrambled letter blocks. Modes of operation provide methods to ensure the message's security during transfer or storage. Here are some common approaches −
ECB (Electronic Code Book) − Think of it as using the same lock for each safe you encounter. Each safe (message block) is secured with the same key, resulting in identical blocks in your message remaining identical after encryption.
CBC (Cipher Block Chaining) − Here, imagine safes linked together with chains. The lock for each safe depends on the lock of the previous safe. This creates a strong chain where even knowing parts of the message won't reveal the original message, as the encryption is interconnected.
Cipher Feedback (CFB) − Unlike encrypting an entire message at once, CFB encrypts smaller parts of it. This allows flexibility for messages of various lengths.
Output Feedback (OFB) − Similar to CFB, but instead of using the encrypted message parts, OFB generates a continuous stream of random data (keystream). This keystream is mixed with the plaintext to create the ciphertext, resembling a constant flow of secret codes.
CTR (Counter) − This mode transforms a block cipher into a stream cipher. It utilizes a counter that continuously increments, generating a unique key for every block. This key is combined with the plaintext to create the ciphertext. Think of it as a ticking counter that produces new secret codes for each portion of the message.
Components of Block Cipher
The Modern Block Cipher consists of the following components −
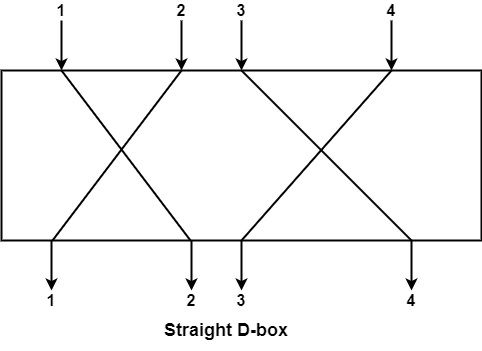
D−boxes − A D−box is a type of permutation box that shares characteristics with conventional transposition ciphers. D-boxes switch around bits. D-boxes come in three different varieties, which are as follows −
Straight D-box − It generates, permutes, and supports n outputs from n inputs. Here, the first input to be output is the second input following permutation. The input's first letter is changed to second, the third to fourth, and the fourth to third. There are n! possible ways to map D-box.
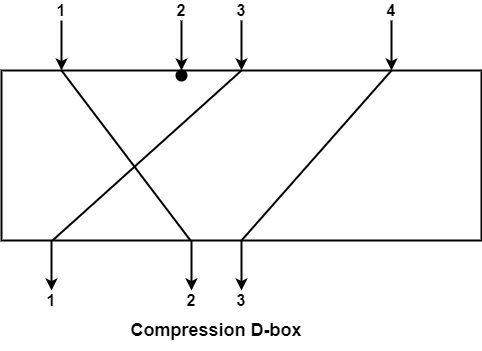
Compression D-box − A compression D-box is one that has m outputs and n inputs, where m<n. Many inputs are blocked and are not sent to the output. When permuting bits and reducing the number of bits needed for the following step are required, compression D-boxes are used.
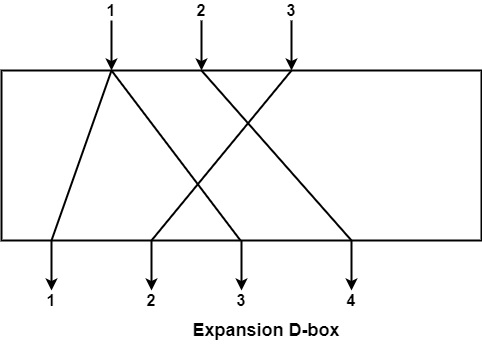
Expansion D-box − This is a D-box that has n inputs and m outputs, where m>n, or multiple inputs connected to multiple outputs, is utilized when bit transposition is needed and the number of bits increased for the subsequent step.
S−boxes − These are substitute boxes that are identical to the cipher for substitution. An S−box accepts n−bit words as inputs, but it can also output m-bit words, where m and n are not exactly the same.
Circular Shift − Modern block ciphers also include circular shift, which can be either left- or right-shifted. Each bit in an n-bit word with m positions is shifted to the left in a cyclical left shift, deleting the leftmost m-bits to become the rightmost bits.
Encryption and Decryption of Block Cipher
Block cipher for encryption and decryption is just like to convert a message into an encrypted message or code. Here is how it works −
First, the message is broken into fixed-sized blocks. Each block has a set amount of characters, often 64 or 128 bits.
The message's blocks are then jumbled using the block cipher technique. This algorithm randomizes the characters in the block using a secret key. The key functions as a customized recipe, determining exactly how the characters are jumbled.
Depending on the mode of operation selected, additional actions may be taken to improve security or meet special requirements, such as encrypting large messages or ensuring uniqueness.
This procedure is done for each block of the message until the entire message is encrypted.
The outcome is a series of scrambled blocks that make up the ciphertext. This ciphertext represents the encrypted form of the original communication.
The secret key that was used for encryption needs to be in the control of someone in order to decrypt the message and show the original text. It is almost impossible to decode the ciphertext and understand the original message without the key.
Example using Block Cipher
Let's try an example with a block cipher called the "Number Shifter."
Below is the steps of how the Number Shifter works −
Let us say we have a secret key, and it is the number 5.
So now we have a message that we need to encrypt, like 123456.
And to encrypt this message with the help of Number Shifter −
To encrypt it
We will take each number in the message and add 5 to it.
And then 1 will become 6, 2 will become 7, 3 will become 8, and so on.
So now 123456 will becomes 67891011 when encrypted with the help of Number Shifter with a key of 5.
To decrypt it
Now we will take every number in the encrypted message and subtract 5 from it.
So it will sutract every number then 6 will become 1, 7 will become 2, 8 will become 3, and so on.
At the end the decrypted message for 67891011 will become 123456 again.
Different types of block ciphers
While there are many different types of block ciphers available, but only a few are known to the public. They vary in usage and popularity because some were created more recently than others. The most generally known and used types of block ciphers are as follows −
DES, or Digital Encryption Standard − It was a popular block cipher during the 1990s. The main reason it is now considered as a failed block cipher is because of its small key size.
Triple DES − Another technique based on multiple DES applications is called Triple DES. While it is less effective than the most recent, faster block ciphers available, it is still a recognized block cipher.
Advanced Encryption Standard (AES) − The relatively recent Advanced Encryption Standard (AES) block cipher is based on the Rijndael encryption algorithm, which took first place in the AES design competition.
IDEA − With a block size of 64 and a key size of 128 bits, it is a block cipher that is effectively strong. IDEA encryption is used by many programs, including the Pretty Good Privacy (PGP) protocol in its early versions. Due to copyright concerns, the IDEA scheme's adoption has been limited.
Twofish − This block cipher method makes use of a variable-length key with a block size of 128 bits. It was a finalist for the AES. Its foundation is the 64-bit block cipher Blowfish from earlier times.
Serpent − A block cipher that was a finalist in the AES competition, including a block size of 128 bits and key lengths of 128, 192, or 256 bits. Compared to other block ciphers, its architecture is more secure, but it is slower.
So DES and AES are two of the most widely used and important block ciphers.
Applications of Block Ciphers
Data Encryption
During transmission or storage, block ciphers are frequently used to encrypt sensitive and private data, like financial information and passwords. This process transforms readable data into a scrambled and encrypted format. Decryption of encrypted data requires authorized access via private keys.
File and Disk Encryption
Block ciphers can also be used to encrypt complete disk drives and files, protecting their data from attackers. Block ciphers are used by encryption programs like BitLocker and TrueCrypt to secure data and make it unreadable without having the proper privileges.
Virtual Private Networks (VPNs)
VPNs encrypt data sent between linked devices over the internet using block ciphers. By doing this, data privacy is protected during transmission and unwanted access is avoided.
Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
SSL and TLS protocol also use block ciphers to encrypt data transferred over the Internet between a web browser and a server Confidential information, such as banking information and login credentials. It is protected from possible hacking by this encryption.
Digital Signature
Block ciphers are used in digital signature technology to ensure the authenticity and authenticity of electronic documents. Each document created using this encryption technique has a unique signature that can be used to confirm its authenticity and detect illegal changes.
Drawbacks/Disadvantages of Block Cipher
Block ciphers are not ideal in every situation because of a few reasons −
Only a certain quantity of data can be used by Block Cipher at once. It becomes complicated if you have more data than that.
For the same data and key, they always generate the same outcome. This might be dangerous if patterns are identified by someone.
Sometimes, more details is required to validate the block cipher. However, these additional stuff can sometimes make it simpler for attackers to crack the code.
You need to use great care when handling secret keys. It is similar to leaving the front door open for hackers if they are weak or poorly managed.
Block ciphers can be applied in many ways, and each method has specific challenges. Making the incorrect decision or performing it incorrectly can lead to problems.
As computers becoming smarter, deciphering the secrets of block ciphers becomes easier for them. This means that we must constantly search for new approaches to data protection.
To Continue Learning Please Login