
- Cryptography Tutorial
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Cryptography Useful Resources
- Cryptography - Quick Guide
- Cryptography - Discussion
Cryptography - Vigenere Cipher
An algorithm called the Vigenere Cipher is used to both encrypt and decrypt text. The vigenere cipher is an algorithm that uses a number of linked caesar ciphers to encrypt an alphabetic text. It is based on the alphabets of a keyword. This cipher is a representation of a polyalphabetic substitution. It is simple to understand and use this algorithm.
History and Development
Giovan Battista Bellaso first wrote about the Vigenere cipher, a polyalphabetic substitution cipher, in the year 1553. However, the cipher was mistakenly credited to Blaise de Vigenere in the 1800s; as a result, the Vigenere Cipher became well-known. The autokey cipher, invented by Blaise de Vigenere, is a distinct cipher that bears a similarity to the Vigenere Cipher.
The French term for it was "le chiffre indechiffrable," which translates to "the indecipherable cipher." It remained intact for three centuries until Friedrich Kasiski published a general deciphering technique in 1863.
Al−Qalqashandi wrote about poly alphabetic substitution ciphers for the first time in the 14th and 15th centuries. Nonetheless, Lean Battista Alberti's Alberti cipher is the first poly alphabetic replacement cipher that has been properly described. The first polyalphabetic substitution, or Alberti cipher, was developed in order to encrypt a message in a way that could conceal the letter frequency distributions. This innovation completely changed the field of cryptography. Since frequency analysis was the only known method of breaking ciphers at the time, it effectively stopped anyone from deciphering the system.
The most well−known poly alphabetic substitution cipher is the Vigenere cipher, which has been cracked despite standing for a very long period. The Vigenere cipher is still applicable for less serious uses, although it is not utilised in any serious cryptography context these days.
Methods of Vigenere Cipher
There are basically two different methods to perform Vignere Ciphers. Let us see these methods one by one in the below section −
Method 1
In this method, the encryption and decryption are carried out using the vigenere table (26 X 26 matrix) once it is given.
Example: The plaintext is "TUTORIALSPOINT", and the key is "KEY".
As long as the length of the plain text is less than the new key, a new key is generated by repeatedly using the given key in a circular manner.
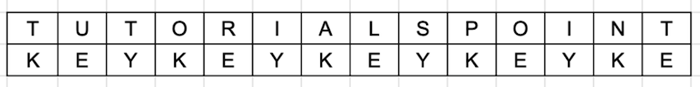
Encryption Process
The initial letter of both the plaintext and the key are concatenated. The vigenere table's alphabet of "D" is intersected by the plain text column "T" and the key row "K," making "C" the first letter of the ciphertext.
In a similar manner, the second letter of the key and the plaintext are merged. The second letter of the ciphertext is "Y" since the alphabet of "Y" in the Vigenere table is intersected by the plain text column "U" and the key row "E."
This procedure keeps on until the plaintext has been extracted.
Ciphertext = DYRYVGKPQZSGXX
Decryption
The row of keys in the Vigenere table is used for decryption. Choose the row containing the key letter first, then identify where the ciphertext letter is located in that row. Finally, choose the column label of the matching ciphertext as the plaintext.
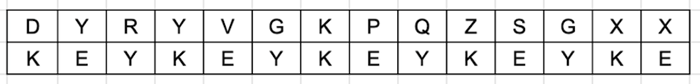
For example, the first plaintext letter is "T" if the key is "K," the ciphertext is "D," and this ciphertext letter appears in column "T."
The next letter is "E" in the key row, "Y" in the ciphertext, and this ciphertext letter appears in column "U," indicating that "U" is the second plaintext letter.
This process never ends until the ciphertext is complete.
Plaintext = TUTORIALSPOINT
Method 2
In the event that the Vigenere table is unavailable, the encryption and decryption process is carried out using the Vigenar algebraic formula, which transforms the letters (A-Z) into numbers (0-25).
Encryption Formula
Ea = (Pa + Ka) mod 26
Decryption Formula
Da = (Ea - Ka) mod 26
In this case, we will add 26 to the negative number if the (Da) value ever goes negative (-ve).
In which,
E stands for encryption.
D stands for decryption.
P stands for plaintext.
K stands for key.
Note that, as the table below shows, "a" stands for the offset of the ath letter.

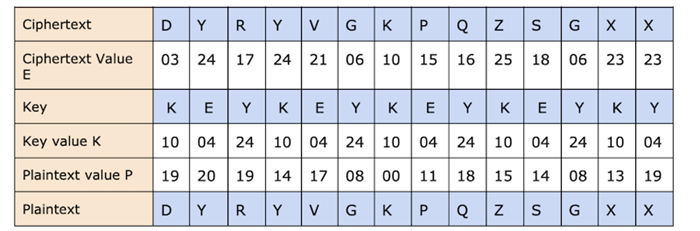
For example, "TUTORIALSPOINT" is the plaintext and "KEY" is the key.
Encryption: Ea = (Pa + Ka) mod 26
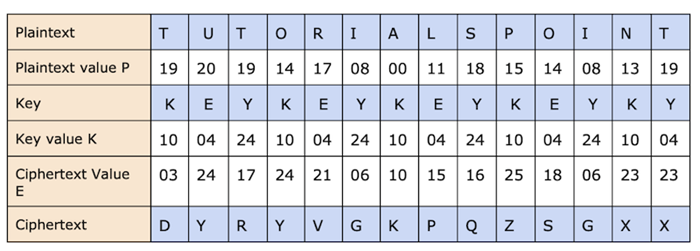
Decryption: Da = (Ea - Ka) mod 26
In this case, we will add 26 to the negative number if the (Da) value ever turns negative (-ve). such as the ciphertext's third letter;
Cryptanalysis
Like all other polyalphabetic ciphers, the Vigenere cipher's basic principle is to mask the letter frequency in the plaintext in order to obstruct a simple application of frequency analysis. For example, one may guess that P corresponds to e since e is the most often used letter in English if P is the most frequent letter in a ciphertext whose plaintext is in English. However, basic frequency analysis is defeated by the Vigenere cipher, which can be used to encrypt e as distinct ciphertext letters at different points in the transmission.
The recurring nature of the Vigenere cipher's key is its primary drawback. Should a cryptanalyst accurately determine the length of the key, the cipher text can be interpreted as n interleaved Caesar ciphers, each of which is easily cracked on its own. The key length can be found by brute forcing every value of n. Alternatively, the Friedman test and the Kasiski examination can be used to estimate the key length.
Strengths of Vigenere Cipher
The cipher masks the letter frequency in plaintext.
The basic goal of this cipher, like most previous poly alphabetic substitution ciphers, was to mask letter frequency such that frequency analysis techniques are considerably limited.
Largely unbreakable without method knowledge.
It is quite challenging to find the secret using anything other than brute force techniques if you are not familiar with the Friedman test or the Kasiski approach.
Truly uninterrupted for three centuries.
Wide key space
The length of the key is denoted by k, and the key space is 26k.
Weaknesses of Vigenere Cipher
The main flaw that causes other flaws is the key's repetitive nature.
It is considerably simpler to estimate the length of the key because it repeats.
Compared to brute force methods, the length of the key can be discovered much faster by using the Friedman test and the Kasiski examination.
A running key cipher, which is essentially a Vigenere cypher but where the key is longer than the message−typically a passage from a book or something similar−or a one−time pad could be used instead.
To Continue Learning Please Login